Overview
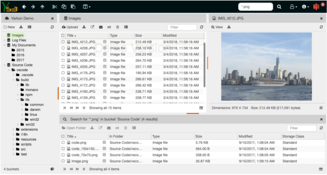
Use Yarkon to upload, download and share documents, manage buckets and create folders – anything that you normally do with S3 – with a fluent, intuitive and feature rich user experience, similar to what you have when using your PC. Drag & drop, context menus, copy-paste, multiple upload/download, it is all there.
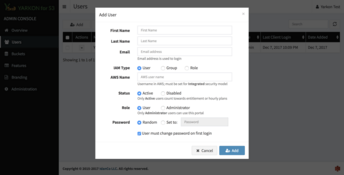
Yarkon enables everyone in your organization to use your S3 storage without provisioning access to the AWS console/account and without sharing any sensitive keys with end users; all that while strictly following the permissions granted by the account administrator using the IAM service, and with full support to groups and roles.
The system consists of two main modules:
- The Yarkon Browser application, the front end used by all end users.
- The Yarkon Admin Console server application, responsible for account administration tasks.
To learn more about the client experience with Yarkon, check out the Demo Application - it is using the infrastructure of Yarkon Cloud and is functionally identical to it.
Yarkon Versions
All versions of Yarkon include a FREE trial, and convenient "Pay as you go" monthly subscriptions, as well as AWS Marketplace subscriptions. You can always get started with the FREE Tier of Yarkon Cloud, and then decide which version is right for you.
Yarkon Cloud is a Software as a Service solution, allowing users to access their AWS S3 buckets using our HTML5 based front-end application. All you need is a subscription - FREE tier is available - and a web browser.
Yarkon Server is a self-hosted solution: you host it in your own AWS account. You deploy it in an EC2 instance within your VPC, and from thereon it operates independently. Yarkon Server has no external dependencies.
Yarkon Docker is a docker based deployment of Yarkon Server: you host it in your own docker infrastructure, using your own orchestration layer. It is the fastest and easiest way to get started with Yarkon.