Folder Level Permissions
Yarkon is the only browser that can properly display an S3 structure that is based on folder level permissions, meaning, Yarkon can show in a single interface folders as the root element.
The permission system for AWS S3 is based on buckets. Folders are a logical concept, and permissions at the folder level is accomplished using conditional policy rules. As such, these policies are more difficult to set up, and as a result, might be error prone. Yarkon recommends using bucket level permissions whenever possible, and using folder level permissions only when there is no better alternative.
To use this feature, you must use the Integrated Security model.
For this example, we will be using a sample organization with a few users, who need to be granted permissions to specific S3 folders based on their respective roles.
Folders
For simplicity, in this example there is only a single bucket, named yarkon-qa-home. In that bucket, there are four folders:
Finance- to be used by finance usersMarketing- to be used by Marketing usersSales- to be used by Sales usershome- represents a folder that users do not have access to
Users
In the organization we have five users:
- The administrator - has access to all folders.
- Fiona F. - a finance user, should have access to the
Financefolder only. - Mark M. - a marketing user, should have access to the
Marketingfolder only. - Sally S. - a Sales user, should have access to the
Salesfolder only. - Sam SM. - a user who does sales and marketing, should have access to both the
SalesandMarketingfolders.
IAM Policies
The following IAM policies are used to set up the required permission system.
Server
The policy for the server is quite standard, with the one change where we limit access to only the single folder. Doing it at the server level is more secure and simplifies future work.
The server policy that is used to limit the access to a single bucket is named yarkons3-console-role-home, and is the following:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowServerToAssumeRole",
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": [
"arn:aws:iam::<account-number>:role/yarkons3-console-role-home"
]
},
{
"Sid": "AllowServerToListIAMEntities",
"Effect": "Allow",
"Action": [
"iam:Get*",
"iam:List*"
],
"Resource": "arn:aws:iam::<account-number>:*"
},
{
"Sid": "AllowServerToListBuckets",
"Effect": "Allow",
"Action": "s3:ListAllMyBuckets",
"Resource": "arn:aws:s3:::*"
},
{
"Sid": "AllowServerToSeeBucket",
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetBucketLocation"
],
"Resource": "arn:aws:s3:::yarkon-qa-home"
},
{
"Sid": "AllowServerToUseBucketName",
"Effect": "Allow",
"Action": [
"s3:GetBucketTagging",
"s3:PutBucketTagging"
],
"Resource": "arn:aws:s3:::yarkon-qa-home"
},
{
"Sid": "AllowServerToSetBucketCORS",
"Effect": "Allow",
"Action": [
"s3:GetBucketCORS",
"s3:PutBucketCORS"
],
"Resource": "arn:aws:s3:::yarkon-qa-home"
},
{
"Sid": "AllowServerToDoS3ActionsInBucket",
"Effect": "Allow",
"Action": "s3:*",
"Resource": "arn:aws:s3:::yarkon-qa-home/*"
}
]
}
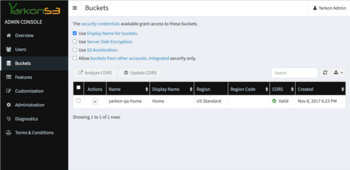
In the Yarkon admin console, the Buckets view looks like this:
Note that the bucket is named, using the Bucket display name feature.
Users
To implement this set up, Yarkon's proprietary policy optimizer has to be able to parse the user policies. For that, the policies must be inline, or, when using the Server or Docker deployments of Yarkon, use the
INLINE_POLICIESenvvariable.
All users are essentially the same, so we will provide a couple of examples here. For the Finance user, who should have access to the Finance folder only, we use the following policy, which is later assigned to a role that would be used for that user, named in this example yarkons3-console-role-home-finance.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowUserToSeeLocationOfBucket",
"Effect": "Allow",
"Action": "s3:GetBucketLocation",
"Resource": "arn:aws:s3:::yarkon-qa-home"
},
{
"Sid": "AllowUserToSeeTheFinanceFolder",
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::yarkon-qa-home",
"Condition": {
"StringEquals": {
"s3:prefix": "Finance",
"s3:delimiter": [
"/"
]
}
}
},
{
"Sid": "AllowListingOfFinanceFolderRoot",
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::yarkon-qa-home",
"Condition": {
"StringLike": {
"s3:prefix": "Finance/*"
}
}
},
{
"Sid": "AllowUserToDoS3ActionInFinanceFolder",
"Effect": "Allow",
"Action": "s3:*",
"Resource": "arn:aws:s3:::yarkon-qa-home/Finance/*"
}
]
}
For the Sales and Marketing user, who has to be able to see both the Sales and Marketing folders, we attach the two policies below, to its role, which is named yarkons3-console-role-home-sales-and-marketing:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowUserToSeeLocationOfBucket",
"Effect": "Allow",
"Action": "s3:GetBucketLocation",
"Resource": "arn:aws:s3:::yarkon-qa-home"
},
{
"Sid": "AllowUserToSeeTheSalesFolder",
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::yarkon-qa-home",
"Condition": {
"StringEquals": {
"s3:prefix": "Sales",
"s3:delimiter": [
"/"
]
}
}
},
{
"Sid": "AllowListingOfSalesFolderRoot",
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::yarkon-qa-home",
"Condition": {
"StringLike": {
"s3:prefix": "Sales/*"
}
}
},
{
"Sid": "AllowUserToDoS3ActionInSalesFolder",
"Effect": "Allow",
"Action": "s3:*",
"Resource": "arn:aws:s3:::yarkon-qa-home/Sales/*"
}
]
}
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowUserToSeeLocationOfBucket",
"Effect": "Allow",
"Action": "s3:GetBucketLocation",
"Resource": "arn:aws:s3:::yarkon-qa-home"
},
{
"Sid": "AllowUserToSeeTheMarketingFolder",
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::yarkon-qa-home",
"Condition": {
"StringEquals": {
"s3:prefix": "Marketing",
"s3:delimiter": [
"/"
]
}
}
},
{
"Sid": "AllowListingOfMarketingFolderRoot",
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::yarkon-qa-home",
"Condition": {
"StringLike": {
"s3:prefix": "Marketing/*"
}
}
},
{
"Sid": "AllowUserToDoS3ActionInMarketingFolder",
"Effect": "Allow",
"Action": "s3:*",
"Resource": "arn:aws:s3:::yarkon-qa-home/Marketing/*"
}
]
}
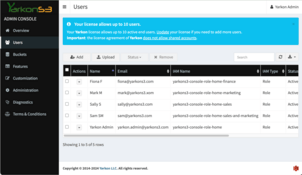
Using the admin console, the Users view should show the following:
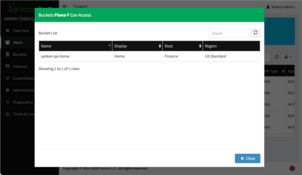
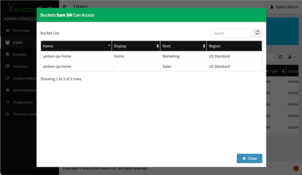
To verify that it worked, check out the buckets for each users:
User Access
The ultimate result - how end users will see their folders using Yarkon, is as following:
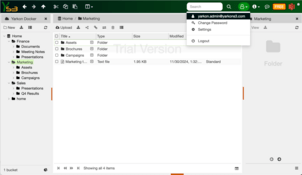
Administrator
The administrator can see all folders. Their root access is the bucket itself.
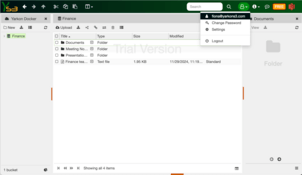
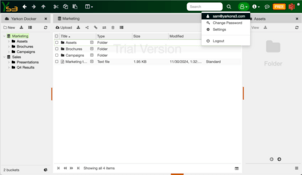
Users
The Finance user Fiona can only see the Finance folder, which is shown as the root of their view. The Sales and Marketing user Sam can see both the Sales and the Marketing folders, but not the Finance folder.