Server side encryption
Yarkon supports all versions of SSE (Server Side Encryption). The full set up is described hereby.
AWS console
On the S3 side, Yarkon expect SSE to be set up following the common AWS guidelines, as illustrated below:
Bucket SSE set to the chosen encryption (Yarkon supports SSE-S3, SSE-KMS and SSE-C).
(Optional, but highly recommended) Bucket policy may be set to disallow non encrypted uploads.
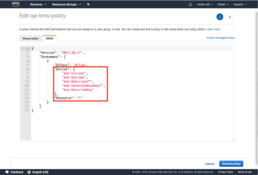
The IAM policy for the Yarkon server role (or the IAM user that is used to grant permissions to the Yarkon user when using the SaaS product) should include the following KMS related permissions:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "*"
}
]
}
This is the most generic and permissive policy. You can start with that, then tighten it further once you see everything working. For instance, you may want to limit the Resource list to the buckets used. The Key related permissions are only needed if you use your own KMS key, so if you do not, you can remove them as well.
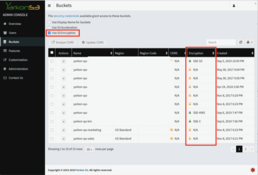
Yarkon admin console
From the Yarkon Admin Console, turn on the SSE feature using the Buckets page. Once the feature is on, the bucket list displayed by Yarkon Admin Console would show the current SSE status of each bucket.
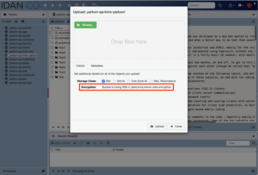
Yarkon client application
The Yarkon client application would recognize it as well.
CORS Rules
For any bucket that uses server side encryption, the CORS rules have to include the header x-amz-server-side-encryption. If you used Yarkon to set up your CORS rules, then this should be set automatically for you. For more, please see CORS rules.