Audit Trail
With Yarkon Server, the system administrator and other privileged users can have full visibility into end users actions, through the Audit Trail feature - see who did what and when, all in your CloudWatch logs.
Unlike other systems like CloudTrail, Yarkon provides a logical, human readable audit trail, showing which actions users made, not just the ultimate changes in S3. Yarkon uses standard JSON formatted entries, making it easy to parse programmatically, in case it is needed.
Below is a sample output of the audit trail feature:
[
{"level":"info","username":"test@yarkons3.com","timestamp":1577924044108,"action":"Log in"},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924045148,"action":"List buckets","cmd":"","params":{}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924045363,"action":"List items","cmd":"","params":{"Bucket":"yarkons3-finance","Prefix":""}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924058695,"action":"List folders","cmd":"","params":{"Bucket":"yarkons3-finance","Prefix":""}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924059256,"action":"List items","cmd":"","params":{"Bucket":"yarkons3-finance","Prefix":"Reports/"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924059423,"action":"Get preview properties","cmd":"headObject","params":{"Bucket":"yarkons3-finance","Key":"Reports/2017-Q2-financial-reporting.xlsx"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924065617,"action":"Download documents","cmd":"","params":{"Bucket":"yarkons3-finance","Keys":["Reports/2017-Q2-financial-reporting.xlsx","Reports/2017-Q3-financial-reporting.xlsx","Reports/2017-Q4-financial-reporting-wip.xlsx"],"ZipFileName":"download.zip"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924071516,"action":"List items","cmd":"","params":{"Bucket":"yarkons3-finance","Prefix":"Presentations/"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924071517,"action":"List folders","cmd":"","params":{"Bucket":"yarkons3-finance","Prefix":"Presentations/"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924071555,"action":"Get preview properties","cmd":"headObject","params":{"Bucket":"yarkons3-finance","Key":"Presentations/Yarkon - Configuration and Flow.pdf"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924071564,"action":"Get document url","cmd":"getObject","params":{"Bucket":"yarkons3-finance","Key":"Presentations/Yarkon - Configuration and Flow.pdf","Expires":"3600"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924083736,"action":"Upload documents","params":{"Bucket":"yarkons3-finance","UploadedKeys":["Presentations/fontawesome-webfont.woff"],"FailedKeys":""}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924085153,"action":"List folders","cmd":"","params":{"Bucket":"yarkons3-finance","Prefix":"Presentations/"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924085181,"action":"List items","cmd":"","params":{"Bucket":"yarkons3-finance","Prefix":"Presentations/"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924085222,"action":"Get preview properties","cmd":"headObject","params":{"Bucket":"yarkons3-finance","Key":"Presentations/fontawesome-webfont.woff"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924090990,"action":"List folders","cmd":"","params":{"Bucket":"yarkons3-finance","Prefix":"Forecast/"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924091335,"action":"Get document properties","cmd":"headObject","params":{"Bucket":"yarkons3-finance","Key":"Forecast/fontawesome-webfont.woff"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924091630,"action":"Move documents","cmd":"","params":{"Bucket":"yarkons3-finance","TargetBucket":"yarkons3-finance","Keys":["Presentations/fontawesome-webfont.woff"],"CopiedKeys":["Forecast/fontawesome-webfont.woff"],"DeletedKeys":["Presentations/fontawesome-webfont.woff"]}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924092536,"action":"List items","cmd":"","params":{"Bucket":"yarkons3-finance","Prefix":"Forecast/"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924092555,"action":"List folders","cmd":"","params":{"Bucket":"yarkons3-finance","Prefix":"Forecast/"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924092575,"action":"Get preview properties","cmd":"headObject","params":{"Bucket":"yarkons3-finance","Key":"Forecast/2017-Q4.xlsx"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924094742,"action":"Get preview properties","cmd":"headObject","params":{"Bucket":"yarkons3-finance","Key":"Forecast/fontawesome-webfont.woff"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924097066,"action":"List items","cmd":"","params":{"Bucket":"yarkons3-finance","Prefix":"Accounting/"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924097067,"action":"List folders","cmd":"","params":{"Bucket":"yarkons3-finance","Prefix":"Accounting/"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924097213,"action":"Get preview properties","cmd":"headObject","params":{"Bucket":"yarkons3-finance","Key":"Accounting/2017-Q2-final.xlsx"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924099027,"action":"Get document properties","cmd":"headObject","params":{"Bucket":"yarkons3-finance","Key":"Accounting/fontawesome-webfont.woff"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924099438,"action":"Move documents","cmd":"","params":{"Bucket":"yarkons3-finance","TargetBucket":"yarkons3-finance","Keys":["Forecast/fontawesome-webfont.woff"],"CopiedKeys":["Accounting/fontawesome-webfont.woff"],"DeletedKeys":["Forecast/fontawesome-webfont.woff"]}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924099605,"action":"List items","cmd":"","params":{"Bucket":"yarkons3-finance","Prefix":"Accounting/"}},
{"level":"info","username":"test@yarkons3.com","timestamp":1577924099634,"action":"Get preview properties","cmd":"headObject","params":{"Bucket":"yarkons3-finance","Key":"Accounting/2017-Q2-final.xlsx"}}
]
Details
- Yarkon Server does not store the audit trail, not even temporarily. It is only proxying the logs directly to your designated CloudWatch stream.
- Audit trail logs are available in near time, usually within minutes from the time the action took place.
- Audit trail logging is non-blocking, meaning that the actions themselves are not pre-conditioned on the logging system.
- As long as you set up Yarkon Server following the recommended best practice of using TLS/SSL, audit trail logs are encrypted end to end, from the user's PC all the way to CloudWatch.
- The system administrator can switch the system on and off, with the change taking effect immediately.
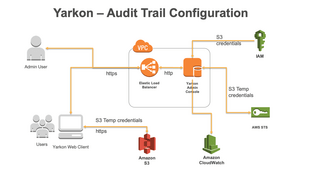
Architecture
The following high-level network diagram describes the architecture of the audit trail feature of Yarkon Server.
Permissions
The Audit Trail feature requires you to use Integrated or Federated security. This is to ensure that the best practice for a standards compliant system is followed.
To be able to publish the audit trail log events to CloudWatch, the following permissions must be granted to the IAM role of the Yarkon Server instance:
- DescribeLogStreams
- DescribeLogGroups
- PutLogEvents
If you want Yarkon Server to create the CloudWatch group and/or stream, you also need to grant these permissions:
- CreateLogStream
- CreateLogGroup
In case any of the required permission is missing, the user interface will notify you when you set up the audit trail feature.
These permissions must only be granted to the IAM role of the Yarkon Server instance. They should not be granted to any user.
Below is a sample policy granting Yarkon Server the permissions required for audit trail logging.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowYarkonToUpdateCloudWatch",
"Effect": "Allow",
"Action": [
"logs:CreateLogStream",
"logs:CreateLogGroup",
"logs:DescribeLogStreams",
"logs:DescribeLogGroups",
"logs:PutLogEvents"
],
"Resource": "*"
}
]
}
You can simply copy this policy and attach it to the IAM role used by the instance.